04 - VoWifi Interfaces Links Protocols (New)
- Vikas Shokeen
- Nov 7, 2020
- 7 min read
SWu Interface - Internet Key Exchange version 2 (IKEv2), RFC 7296. We will also cover IPSEC Overview here
S2b Interface - GTP Protocol, PMIP (Proxy Mobile IP), 3GPP TS 29.274
SWm Interface – Diameter Protocol, 3GPP TS 29.273
SWx Interface – Diameter Protocol, 3GPP TS 29.273
S6b Interface – Diameter Protocol, 3GPP TS 29.273
Protocols

SWu Interface

This Interface is used between ePDG and UE
SWu interface is running on IKEv2 – i.e. Internet Key Exchange
It uses IKEv2 protocol to establish IPSec tunnel between ePDG and UE
IKEv2 is used to perform IPSEC authentication, session development and negotiation of IPSEC Tunnels
It is a secure Interface from Core Networks towards users in non-3GPP access network
Since Users or UE is residing in non-3GPP access networks , Additional Security via IPSEC Tunnel & IKEv2 protocol is implemented via Encryption of traffic & Use of cryptographic techniques for :-
• Protect User Privacy , provide confidentiality
• Ensuring Network Sanity & Integrity
• Error Free authentication
• Anti-replay protection
These IPSEC tunnels are supported on both IPv4 & IPv6 IP Addresses . These uses AH & ESP Protocols . Typically VoWifi uses UE to connect to ePDG Public IP on Port 500 and 4500 for Setup and IPsec encrypted packets transfer . Which Means these Ports has to be allowed on both UE Side CPE & ePDG Side firewalls
As far as specs are concerned , You can refer to RFC 5996 / 7296 for more details on IKEv2 and IPSec ESP encryption used here
What is IP Sec ?

IPSEC Stands for Internet Protocol Security (IPsec) , Well it allows us to secure the network layer IP traffic . Since VoWifi traffic transit via Internet , It becomes important for us to protect it otherwise Man in Middle can decode you traffic can listen all your calls and read your SMS during transit
Below features are offered by IPSEC :-
• Confidentiality : IPSEC ensures that No one but the sender and receiver will be able to read our data by encrypting our data
• Integrity : IPSEC ensures that No body changes the data in our packets while its travelling from Internet . The sender and receiver will be able to verify whether Data have been modified during the transit using a hash value
• Authentication : IPSEC helps UE and ePDG to ensure that they are speaking to right entity & Not some one spoofed in Internet , Here both UE and ePDG authenticate each other
• Anti-replay : At worst , Even if a packet is encrypted and authenticated , the Middle man may attempt to catch and re-send those packets to make fool of receiver . IPsec protects this well
To do these things, IPSec uses two protocols which are defined by the IETF :-
Authentication Header (AH) :- Here , AH provides a method for authentication , Here AH authenticates IP headers and their payloads . AH does below tasks :-
a) Data integrity : a message digest that is generated by an algorithm such as HMAC-MD5 or HMAC-SHA
b) Data origin authentication : using a shared secret key to create the message digest
c) Replay protection : Replay protection is provided by using a sequence number field with the AH header
2. Encapsulating Security Payload (ESP) : ESP protocol handles Encryption & Authentication . ESP can be used in various modes such as :-
• Encryption only
• Authentication only
• Both Encryption and authentication
ESP in fact provides more advanced Security by offering Both Encryption and authentication
What is IKE?

First thing First , Why do we need IKE ? The aim of the Internet Key Exchange (IKE) is to generate the same symmetrical key independently for both parties. This key then encrypts and decrypts the standard IP packets passing thru tunnels . A Security Association (SA) is the outcome of an IKE negotiation.
Well , IKE and IPSEC work in conjunction with each other. IKE helps in establishing SA (security association) for either ESP (Encapsulated security protocol) or AH (Authentication header) which are part of IPSec protocols . IKE is a network security protocol designed to dynamically exchange encryption keys and create Security Association (SA) between UE & ePDG . These Security Associations or SAs can be established dynamically and removed at a negotiated time period
S2b Interface
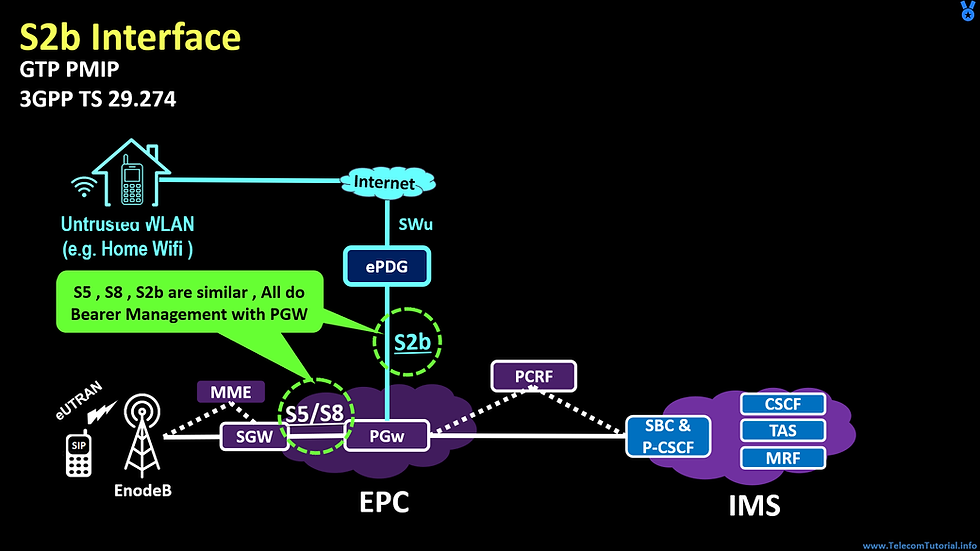
Now, We are going to discuss very interesting concept of Bearer management . Here we will see similarity between s5/s8 & s2b
What is s5/s8 interface
• Basically , s5/s8 is Interface between the S-GW and P-GW ( i.e. used in EPC LTE Network – 4G Network )
• The both are technically same , we call it s5 if it’s local & we call it s8 if its used for roaming scenario
What is s2b interface
• S2b Connect ePDG to the P-GW & it’s used for VoWifi Access
Now , Let’s see similarities between these s5/s8 & s2b
• Both are used to Provide connectivity to PGW for Session Creation
• Both works on similar Protocol and uses same messages for Bearer creation & Deletion
Bearer Formation for VoWifi

Now , Let’s understand the Bearer formation for VoWifi . 'Bearer' in the dictionary means "Carrier" or "Porter" which carries something from a point to another point. Under the context of communication technology, I would define the 'Bearer' as a 'pipe line' connecting two or more points in the communication system in which data traffic follow through.
QCIs are correlated with bearer in EPC network. There is separate bearer and QCI for all type of traffic such as IMS SIP Signaling , IMS Voice Call & IMS Video Call . There are 2 types of bearers – Default & Dedicated . Refer to this diagram where we are going to discuss very interesting concept of Wifi Calling . While VoLTE have End to End Bearers for SIP , Voice & Video Call , i.e. These separate 3 bearers exists between UE to Radio , Radio to SGW , SGW to PGW . The same thing doesn’t happen with VoWifi . In VoWifi , These bearers are created between ePDG to PGW only . All type of traffic viz , SIP Signaling , Voice & Video comes via IPSEC tunnel and terminated on ePDG . Further ePDG map this traffic to various bearers created with PGW . In other words , There are no bearers between ePDG & UE in VoWifi , These separate bearers exists between ePDG & PGW only
Role of these Bearers
• QCI=5 is used for VoLTE IMS Signaling , This is Default EPS Bearer which is established during VoWifi Attach & Registration . This is used for Allocating IP address to UE . This is always connected type bearer
• QCI=1 is used for VoWifi IMS Voice Call , While QCI=2 is used for VoWifi IMS Video Call . These are Dedicated bearers which are created during call & is released once call is over . These offer specific QoS which is guaranteed
S2b Interface
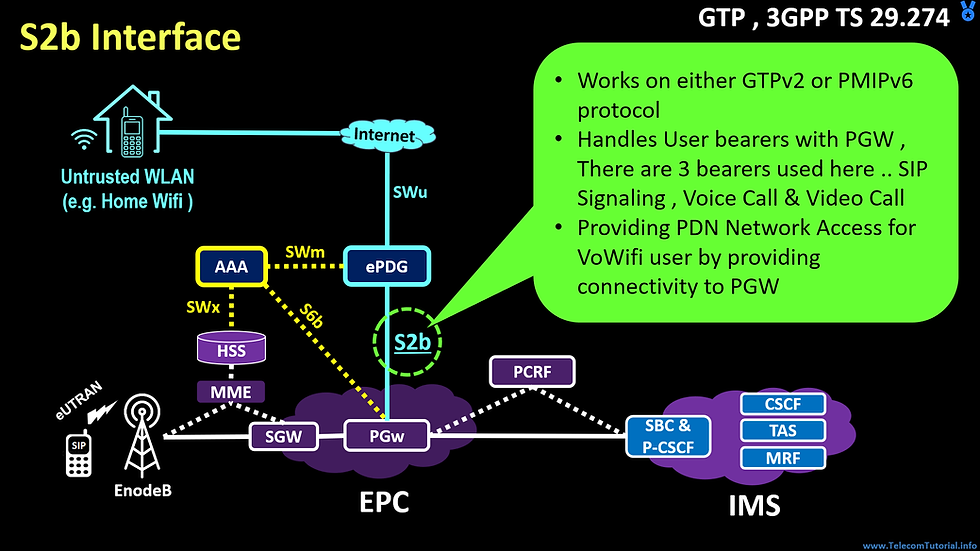
Working of S2b Interface
S2b connects ePDG to P-GW , Its derived from 3GPP TS 29.274 Specs
It Works on either GTPv2 or PMIPv6 protocol
The role of S2b is to maintain User bearers with PGW , There are 3 bearers used here .. SIP Signaling , Voice Call & Video Call
Just like VoLTE , The bearer creation/deletion/modification happens between ePDG and PGW . The Bearer in VoWifi are not End to End , They exist only in core network between ePDG to PGW
QCI-5 based SIP Signaling Bearers is created during VoWifi Attach / Registration , It is released during Detach or Disconnection
Similarly , The Voice or Video Call bearer is created only during call . It’s terminated after call release
S2b is critical link which is used for providing PDN Network Access for VoWifi user by providing connectivity to PGW
SWm Interface
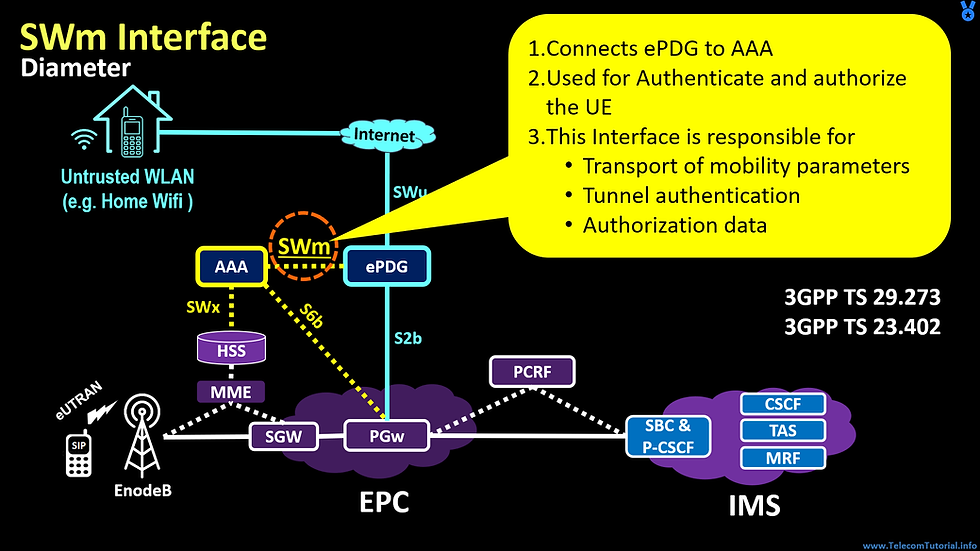
It connects ePDG to AAA ( Full form of AAA is Authentication, Authorization and Accounting server )
It is used for Authenticate and authorize the UE . It uses EAP-AKA method
This Interface is responsible for Transport of mobility parameters between ePDG to AAA , Carrying Tunnel authentication Data & Authorization Users
It is used for Passing Information from HSS to ePDG , For Ex :- HSS may pass static IP Address to user which is passed from HSS to AAA & further AAA to ePDG for Action
You should refer to 3GPP Specs 29.273 & 23.402 for further studies and details on this Interface
SWm Interface - Messages

Let’s understand few messages which are exchanged to make it bit more clear :-
• Diameter-EAP-Request (DER) / Diameter-EAP-Answer (DEA) :- ePDG Send DER with user details , AAA Authenticates & reverts back with User details such as APN Details , QOS , PGW , AMBR & EAP-Payload details
• Authorization-Authentication-Request (AAR) / Authorization-Authentication-Answer (AAA) : ePDG trigger this to AAA for getting most recent service authorization information
• Abort-Session-Request (ASR) / Abort-Session-Answer (ASA) : Used during Detach of User to Abort the session
• Session-Termination-Request (STR) / Session-Termination-Answer (STA) : ePDG Inform AAA that resources are released and user session is terminated
• Re-Auth-Request (RAR) / Re-Auth-Answer (RAA) : It is triggered by HSS whenever subscription data is changed or updated for connected user
SWx Interface

SWx interface is used to connect AAA to HSS
HSS stands for Home Subscriber Server
HSS is repository and Database for all user Information , It includes Authentication & Subscription information for user
In easy words , All Services are defined in HSS , In case customer is not allowed for VoWIFI Service in HSS Profile , The user will not be allowed to use VoWifi service
SWx interface is used by AAA to obtains subscription data of subscribers from HSS Just like SWm , The SWx is used for Authentication & authorization , Main purpose of this Interface is :-
• Registration & De-Registration of User in Network & corresponding update on AAA & HSS
• Transport UEs mobility parameters
• Fetch User authorization data from HSS
• Update the PGW info to support seamless handover between VoLTE to VoWifi and Vice Versa . We will discuss this in detail later on while covering the call flows
S6b Interface

• It Connects AAA & PGW
• In Operator Network , There are multiple PGWs who serve users
Common PGW
• In case VoWifi PDN is established on One PGW & VoLTE PDN is established on another PGW , Handover will not happen between VoWifi to VoLTE
• Here s6b solves real problem .. When ever UE is attached on non-3GPP access , This interface is used to update PGW address to HSS
• With help of this PGW IP Address , We ensure common PGW should selected to serve both VoLTE & VoWifi Service
Future Reading & References

Well now we are at the end of this Module , You can refer to these documents for Future Reading & References
You need to simply type them in google & download PDF copy
RFC 7296
- Internet Key Exchange Protocol Version 2 (IKEv2)
- Basics of SWu Interface
3GPP TS 29.274
- S2b interface by the ePDG to the PGW
3GPP TS 29.273
- 3GPP EPS AAA interfaces
- AAA Links , Descriptions , Format & Usage




Comments